API Overview
A complete guide to understand Okto APIs and integrate them in your application.
Introduction to Okto API
Okto provides a comprehensive set of APIs for integrating Web3 functionality into any application. This guide will help you understand the core architecture, authentication flow, and how to effectively integrate with our APIs.
API Architecture
Okto provides a unified set of REST APIs for all wallet and on-chain operations:
REST APIs
- Description: Calls to the Okto Chain through a BFF service
- Endpoint:
https://sandbox-api.okto.tech - Used for: Authentication, executing user operations (intents), explorer functions (portfolio, wallets, tokens, etc.)
The OpenAPI specification documentation supports interactive elements for all REST APIs. For detailed code examples and implementation, check out the Template Repository.
Authentication Flow
The Authentication Flow is performed on the client-side and consists of these steps:
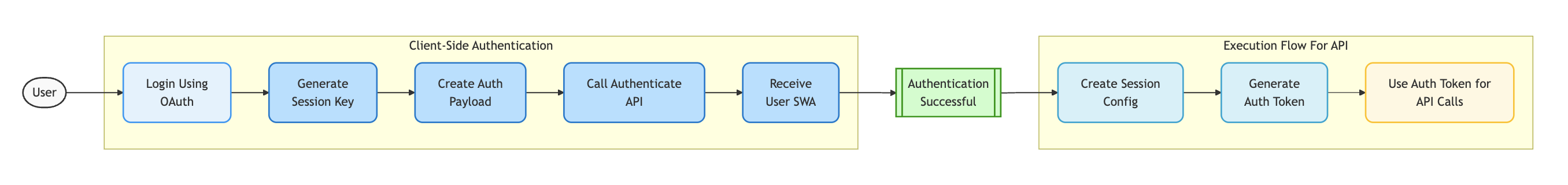
- Login Using OAuth - User authenticates through your chosen OAuth provider
- Generate Session Key - Create a cryptographic key pair for securing the session
- Create Auth Payload - Construct the necessary data with OAuth token and provider. The Auth Payload is a user operation which contains the callData, paymaster details and gas details.
- Call Authenticate API - Call the Okto Authenticate API (GAuth, whatsapp, etc.) with the Auth Payload.
- Receive User SWA - Obtain the user's Smart Wallet Address
At this point, authentication is successful.
For delegated actions and to execute explorer functions and API calls, you will need to store session info and generate auth token. For this you will need to perform these additional steps:
- Create Session Config - Create a session configuration using stored session details and user SWA
- Generate Auth Token - Create the Okto Auth Token needed for API calls
- Use Auth Token for API Calls - Include the token in all subsequent API requests
The Okto Auth Token generated at the end of the authentication flow is necessary for all explorer functions and API calls.
To immediately test out the explorer functions, you can generate an auth token using the Okto Auth Token Generator tool described below.
Using the Okto Auth Token Generator Tool
The Okto Auth Token Generator simplifies the authentication process for testing purposes. This tool handles all the steps above and provides you with an Okto Auth Token.
The tool generates a session private and public key pair that is required for signing operations. If implementing your own authentication flow, store the private key and the userSWA securely!
Using the Auth Token
After successful authentication and the generation of the Okto Auth Token, you will need to include the Auth Token in all subsequent API calls:
# For REST APIs
curl -X GET https://sandbox-api.okto.tech/api/oc/v1/wallets \
-H "Authorization: Bearer <your-okto-auth-token>"Getting Started
To start integrating with Okto APIs:
Set up your environment:
- Create an Okto Developer Dashboard account
- Generate API credentials
- Fund Okto Credits using the faucet on dashboard.
- Enable chains and tokens for your application
Authenticate:
- Use the Okto Auth Token Generator to obtain an authentication token
- Or follow our Sample Implementation to implement authentication in your code
- A session is created for the user and client, with a default validity of 10 days. However, this duration can be customized as needed
- Store your session keys securely
Make API calls:
- Use the Auth Token in all subsequent requests
- Follow our API documentation for specific endpoints
Explore API
Need further assistance?
If you have additional questions or require further support, please join our Discord community and open a support ticket in the support-ticket channel.